Why You Don't Need 2 Factor Authentication
TL;DR because 2FA == password manager.
2FA, as many other things in infosec, is full of myths and stereotypes. I stumbled upon this link where lots of people demand bitbucket to add 2FA. For what? Let’s talk about some myths of 2FA.
Myth 1. What you “know”, what you “have”, blah blah
Wikipedia page about multi factor auth. There are no “knowledge” and “inherence” factors, there’s only possession factor. You possess a password by having it in your neurons (or whatever used for memory), you also possess your fingerprints (fingers happen to be attached to your body since you were born).
Therefore there are no “3 categories” that can be used for authentication, there is unlimited number of factors with different “features”. Let’s mention some of them:
-
Password - stored in your memory, easy to forget, often reused, often not complex enough. A human being can only remember few dozens of complex enough passwords.
-
Hardware token - stored in your backpack, not hard to lose or break, almost impossible to backup.
-
Fingerprint - is username, not password. Should never be used in remote systems like web apps. Refrain from using it in physical access systems too - in near future faking perfect fingerprints is more likely than mind stealing your passwords.
-
SMS/Email code - here you have to rely on few other guys in the middle who possess your codes as much as you do - telecoms and email providers. Codes sent by SMS (like Authy) are not 2FA, it’s 2 step verification, pretty much pointless and expensive.
-
Whitelisted IP address - trustworthy, but beware of CSRF requests and DNS rebinding attacks.
to be continued
Myth 2. 2FA makes my account more secure with no strings attached
Technically it does because it adds extra authentication step but you don’t see the big picture yet:
-
It requires you to type a code every time and wastes your time
-
If you lose HOTP seed it is up to admins to give you second chance to access your account
-
Doesn’t stop malware and viruses - Schneier wrote extremely good insight back in 2005
-
Major design mistake - TOTP authenticators generate just 6 digits - OTP bruteforce works like a charm and takes less than 3 days. On top of that 30 seconds limit is quite silly - it doesn’t make bruteforce any harder - just do the math and you will see.
There’s no way to stop bruteforce not locking the account. The real user will be locked out as well, and it’s again up to admins if they decide to spend their time on your ID verification. Good HOTP should have bruteforce “protection” out-of-box, 6 letters [a-zA-Z0-9] give 56800235584 combinations and require hunders of years of bruteforce.
Recap (read this before commenting, ok?)
A 2FA app is essentially a password manager. A 2FA seed/code is essentially a password. “Time-based” thing does not add any security, and 6-digits thing makes security even worse. 2FA is obscure, inconvenient, hard to backup, bruteforce-able password manager.
You don’t need 2FA, all you need is a unique complex password and a password manager.
There’s no plausible attack scenario where simple password + 2FA is better than good complex password alone. Why?
-
If the attackers managed to infect your computer with malware, they can wait a couple of days until you type a valid OTP code. “Be hacked right away” vs “be hacked next week” is not major advantage. Out-of-band 2FA is another story though and I didn’t see it implemented properly anywhere.
-
If the attackers hack your email box, now they can set a new password, indeed. This could be mitigated with some “Never remind me password” option - stop asking Bitbucket and others to implement 2FA, better ask them to add such option.
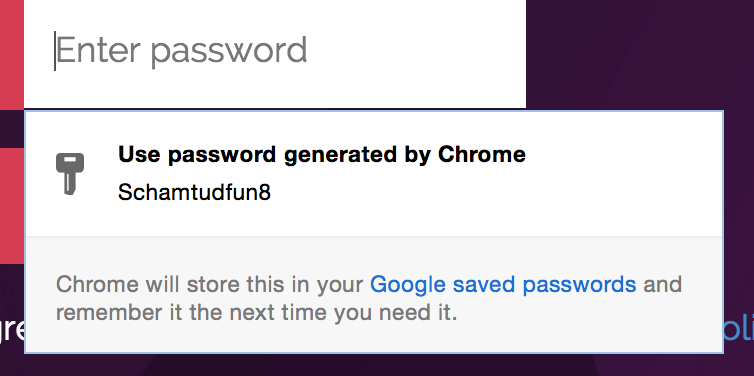
Thanks Chrome, this is the future:
Tweet @homakov to tell how wrong I am.
P.S. 2FA comes in handy if you know your support guys (likely) use bad passwords and “You must set 2FA” is just another way to say “You must use a password manager”.